
MMS • Nsikan Essien
Google Cloud announced the preview release of Direct VPC egress for Cloud Run. The capability enables traffic from Cloud Run containers to access Virtual Private Cloud (VPC) networks without Serverless VPC Access connectors, allowing for cheaper connection routes with larger bandwidth.
Cloud Run is a fully managed container orchestration platform. Built on Knative, the service offers a serverless deployment environment for stateless microservices.
Historically, access to resources within a VPC Network from Google Cloud serverless environments has required the use of Serverless VPC Access connectors. The Access connectors allow traffic from services like Cloud Run, App Engine or Cloud Functions to enter the VPC without flowing through the public internet. This works by providing a fleet of managed virtual machines to proxy traffic to the relevant IP addresses within the VPC. While these virtual machines can provide a robust route into the network, they are billed per hour the instances are available, irrespective of their level of utilization, and add an extra hop in the traffic route. Additionally, once scaled up, Access Connectors do not scale down. Direct VPC egress is a newer approach that aims to overcome these drawbacks.
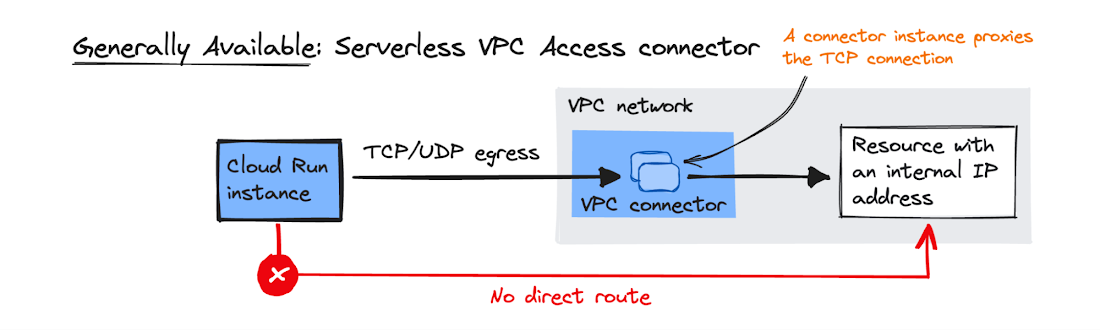
An illustration of VPC connectors proxying traffic from a Cloud Run Instance into a VPC (Source: Google Cloud News Blog Post)
With Direct VPC egress, Cloud Run instances get assigned IP addresses within the target VPC network and have their traffic routed directly. Additionally, Direct VPC egress acts as a firewall, only allowing connections initiated by the Cloud Run instance rather than from resources within the VPC. This allows a faster network path with greater throughput and reduces costs as the charges are only for the traffic rather than any virtual machine instances. The recommended deployment setup for this feature is into a subnet with 4 times as many unused IP addresses as Cloud Run instances.
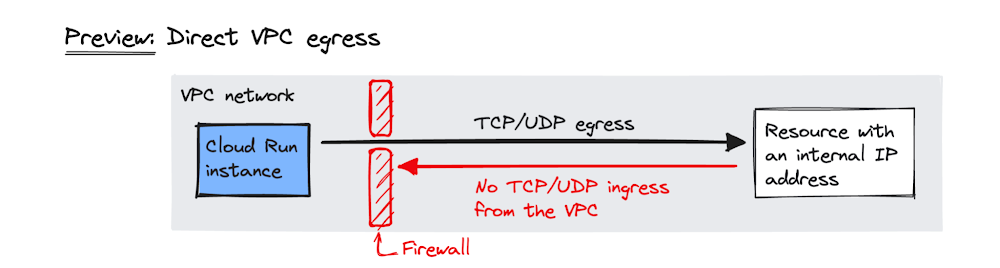
An illustration of Direct VPC egress from a Cloud Run Instance into a VPC (Source: Google Cloud News Blog Post)
The feature, which is still in preview at the time of writing, has some limitations. A few of note are the instance limit of 100 and incompatibilities with Cloud NAT, VPC Flow Logs and Firewall Rules Logging. Additionally, as part of the preview release, the feature is only available in 5 regions: us-central1, us-east1, europe-west1, europe-west3 and asia-northeast1.
Feedback on the community has been positive with a user cabalos commenting on the r/googlecloud thread:
[We] started testing Direct VPC to replace Serverless VPC. We’re seeing massive latency improvements. On a read heavy app connecting to Cloud SQL and Memorystore, latency is cut in half.
Finally, further information on how to get started with Direct VPC Egress is available on its documentation page.