
MMS • Steef-Jan Wiggers
Article originally posted on InfoQ. Visit InfoQ
Recently AWS announced it would make two changes to Amazon Simple Storage Service (Amazon S3): all buckets in a region will have S3 Block Public Access enabled and access control lists (ACLs) disabled by default. These changes will take effect in April 2023 and will be rolled out by the company in all AWS Regions within weeks.
Amazon S3 is a managed object storage service on AWS, and its S3 buckets and objects have always been private by default. The company added Block Public Access in 2018 and the ability to disable ACLs in 2021 to provide customers more control. In addition, customers can also leverage AWS Identity and Access Management (IAM) policies to manage access.
Both S3 Block Public Access enabled and access control lists (ACLs) disabled were default settings in the console. As of April 2023, they will become the default for buckets created using the S3 API, S3 CLI, the AWS SDKs, or AWS CloudFormation templates.
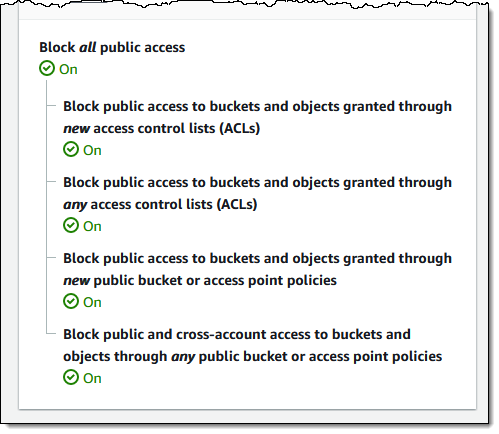
Source: https://aws.amazon.com/blogs/aws/heads-up-amazon-s3-security-changes-are-coming-in-april-of-2023/
Through these new defaults, customers who do require applications to have their buckets publicly accessible or use ACLs must deliberately configure their buckets to be public or use ACLs. To configure these settings, they must update automation scripts, AWS CloudFormation templates, or other infrastructure configuration tools.
Other public cloud providers Microsoft and Google also offer managed storage services with security defaults. For instance, Azure Storage accounts, by default, do not allow public access to containers. However, the default configuration for an Azure Resource Manager storage account permits a user with appropriate permissions to configure public access to containers and blobs in a storage account. Similarly, public access to Google Cloud Storage buckets can be prevented.
An IT & Infosec Consultant, regarding the defaults, tweeted:
Make it easy to do the usually right thing and harder to do the usually wrong thing.
In addition, a respondent on a Reddit thread commented:
Good security to make it the default. I hope a lot of lab blogs get their instructions updated for this, or there will be a lot of new AWS users confused as they are learning. I’ve seen so many labs use public buckets.
Lastly, more details on the changes are available on the FAQ page.