MMS • Steef-Jan Wiggers
Article originally posted on InfoQ. Visit InfoQ
Microsoft has announced that its Azure Application Gateway, a cloud-based solution that provides secure, scalable, and reliable access to web applications, now supports mutual Transport Layer Security (mTLS) and Online Certificate Status Protocol (OCSP).
The mTLS support ensures that both the server and client authenticate each other before establishing a secure connection. At the same time, OCSP checks the status of digital certificates in real time, reducing the risk of cyber attacks. Implementing mTLS and OCSP in Azure Application Gateway enhances security, improves compliance, and reduces the risk of cyber attacks.
The additional layer of security provided by mTLS ensures that the authenticity of both the client and server is validated, making it more secure than TLS – suitable where organizations follow a zero-trust approach.
Application Gateway supports certificates issued from both public and privately established certificate authorities. It also supports TLS termination at the gateway, which improves performance and reduces resource consumption on the backend servers.
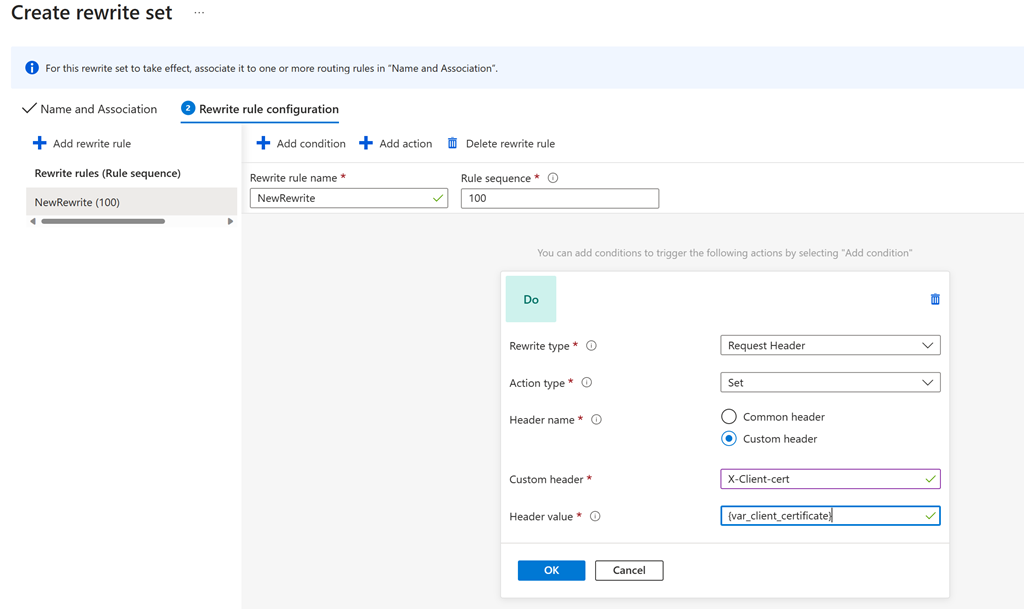
With OCSP support in the application gateway, users can have it send a client certificate to the backend application server in case it needs client certificate information for audit purposes or may want to issue a token or cookie to a client certificate. To achieve that, users can set up a rewrite rule to send the client certificate as an HTTPS header.
Furthermore, with OCSP support, users can verify the status of the client certificate in real time. This can prevent man-in-the-middle attacks by ensuring that the present certificate is still valid and has not been compromised.
Rajesh Nautiyal, a Senior Technical Program Manager, explains in an Azure blog post:
When a client initiates a connection to an Application Gateway configured with mutual TLS authentication, not only can the certificate chain and issuer’s distinguished name be validated, but the revocation status of the client certificate can be checked with OCSP (Online Certificate Status Protocol). During validation, the certificate presented by the client will be looked up via the defined OCSP responder defined in its Authority Information Access (AIA) extension. In the event the client certificate has been revoked, the application gateway will respond to the client with an HTTP 400 status code and reason. On the other hand, if the certificate is valid, the request will continue to be processed by the application gateway and forwarded to the defined backend pool.
To enable mTLS and OCSP on Application Gateway, customers must configure their backend servers with certificates signed by trusted authorities. In addition, they must also upload their root or intermediate CA certificates to Application Gateway.
Microsoft recommends mTLS specifically:
- For communication between Internet of Things (IoT) devices, each device presents its certificate to the other to authenticate.
- In a microservice architecture, making communication between APIs more secure and preventing malicious APIs from communicating with them.
- Preventing attacks like brute force or credential stuffing.
Users can configure mTLS after provisioning an Azure Application Gateway or on an existing one through the SSL setting tab in the portal. Alternatively, they can use PowerShell.
Lastly, more details on Azure Application Gateway are available in the documentation pages and FAQs.