
MMS • RSS
Posted on mongodb google news. Visit mongodb google news
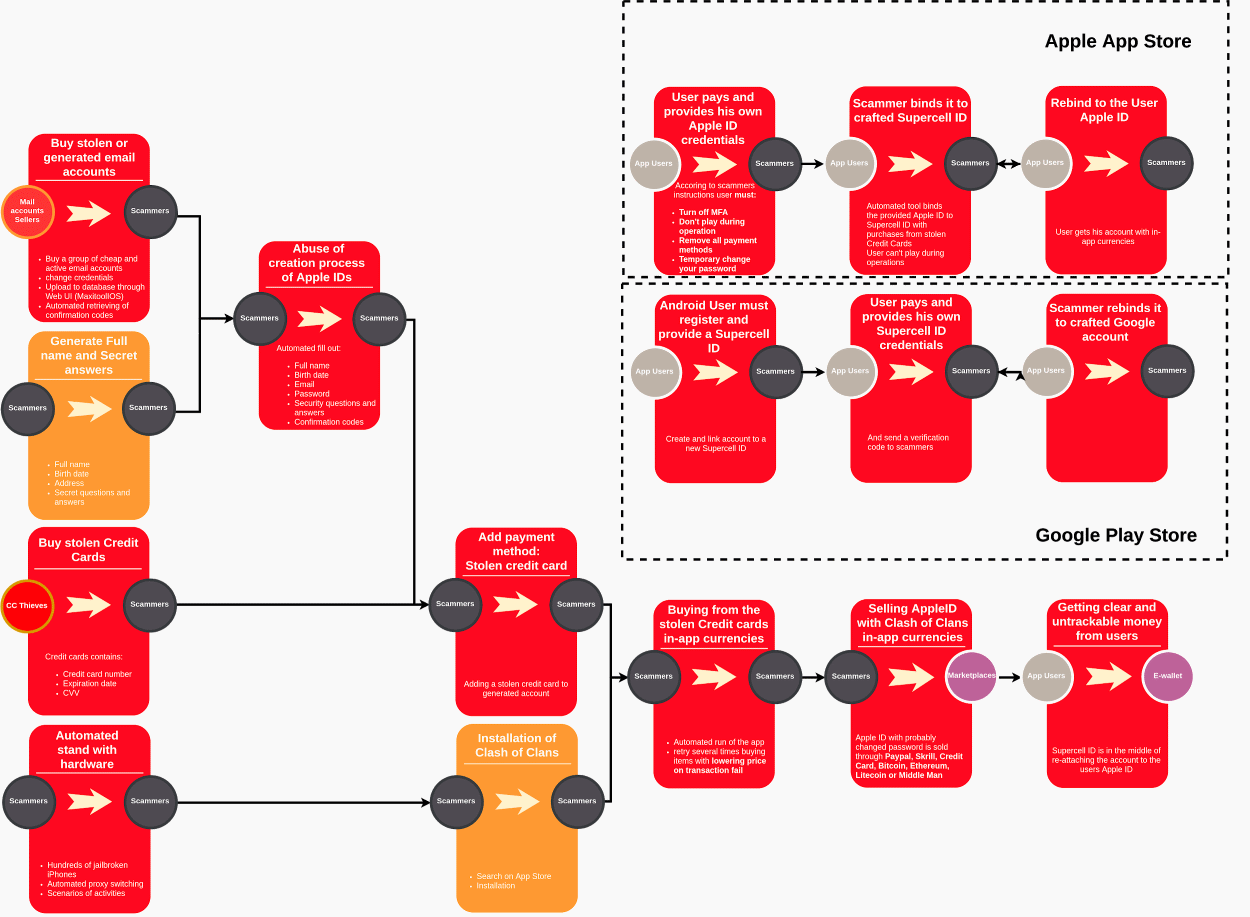
The US Department of Justice, Apple, and game maker Supercell, have been warned of a money laundering ring that uses fake Apple accounts and gaming profiles to make transactions with stolen credit/debit cards and then sells these game premiums on online sites for the group’s profit.
This operation came to light in mid-June when security researchers from Kromtech Security came across a MongoDB database that had been left exposed online without authentication.
“As we examined the database we rapidly became aware that this was not your ordinary corporate database,” said Kromtech researcher Bob Diachenko.
“This database appeared to belong to credit card thieves (commonly known as carders) and that it was relatively new, only a few months old,” he added.
Group was using automated tools to buy game premiums
Diachenko says the group was using a special tool to create iOS accounts using valid emails accounts, then was adding a stolen payment card’s details to one of these new iOS accounts.
The group then ran another automated tool on jailbroken iOS devices to install various games, create in-game accounts, and purchase game features or premiums that they later re-sold online for real money.
The expert says crooks targeted mobile games such as Supercell’s Clash of Clans, Supercel’s Clash Royale, and one game by Kabam named Marvel Contest of Champions.
Details of over 150,000 cards found in the database
Based on the data contained in the database, Diachenko says this automated tool was configured to create accounts specific to users located in Saudi Arabia, India, Indonesia, Kuwait, and Mauritania.
The database also contained 150,833 unique cards entries, each with full card number, expiration date, and CCV, according to a report Kromtech shared with Bleeping Computer before publication.
“Credit cards we found belong to 19 different banks,” Diachenko said. “They were probably bought on the carder markets as they were in groups of round numbers, like 10k, 20k, 30k.”
Blame goes all around
Besides notifying the DOJ and Supercell, Diachenko says he also notified Apple because he also found that the iOS maker was using lax verification measures for the system that adds payment card data to iOS accounts, and hence, making the crooks’ job easier.
The Kromtech expert says that cards with improper names and addresses were easily approved and added to iOS accounts.
But Diachenko also blames the two game makers for not putting in place systems that can detect automated abuse like the one carried out by this group, who, Diachenko says, used a tool named Racoonbot to interact with Supercell games and automate the premium feature buying operations.
Kromtech said that while they saw instructions with rebinding crafted for Google accounts, this particular gang (whose DB we analyzed) was focused on Apple App Story only.
A full report on this gang’s activities with an in-depth breakdown of their operation is available here.
Article originally posted on mongodb google news. Visit mongodb google news