MongoDB has revealed that threat actors gained unauthorized access to corporate systems, warning users that some information may have been exposed in the incident.
In an alert to customers last week, the open source database host said it first detected suspicious activity on 13th December. A subsequent investigation found a suspected data breach had been ongoing for “some period of time before discovery”.
Exact details on the scale or severity of the breach are still to be determined.
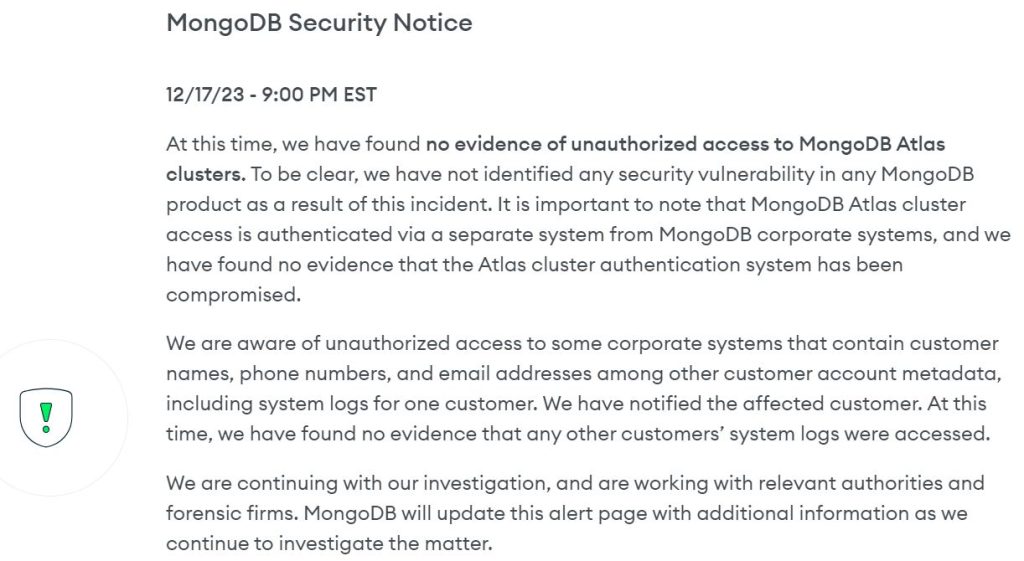
However, MongoDB acknowledged that threat actors gained access to customer information. This included access to customer names, phone numbers, and various other contact details.
“We are aware of unauthorized access to some corporate systems that contain customer names, phone numbers, and email addresses among other customer account metadata, including system logs for one customer. We have notified the affected customer,” MongoDB said.
The organization sought to further calm customer concerns, adding that it has found “no evidence that any customers’ system logs were accessed”.
MongoDB data breach: Atlas clusters are safe
In the immediate wake of the breach notification, concerns arose that threat actors may have gained access to MongoDB Atlas cloud clusters.
The database management firm said a probe over the weekend found no evidence of unauthorized access to the clusters, however. This is because MongoDB Atlas cluster access is authenticated via a separate system from corporate systems, the firm added.
Furthermore, MongoDB insisted that no products across its portfolio have been impacted.
“At this time, we have found no evidence of unauthorized access to MongoDB Atlas clusters,” it said. “To be clear, we have not identified any security vulnerability in any MongoDB product as a result of this incident.”
Customers still advised to remain vigilant
While MongoDB’s full investigation into the incident remains ongoing, the firm recommended that customers “be vigilant for social engineering and phishing attacks” due to the exposure of contact information.
The firm advised customers to activate phishing-resistant, multi-factor authentication techniques.
It also recommended users “regularly rotate their MongoDB Atlas passwords”.
What is MongoDB?
Created in 2007, MongoDB is a document-oriented database which lends itself to scalability and flexibility.
The team who created it, formerly of DoubleClick, helped foster a new way of thinking about databases – by electing to use JSON documents organized into collections, they were able to make database access and complexity a lot easier for consumers.
The advantage of this system is that, unlike in a relational database, a predefined database schema is optional. This means that data structures can be changed quickly without recourse to complex database migrations.
From a customer perspective this system is also handy, as it allows frequently accessed data to be stored in the same place, thus making read operations particularly fast.